It is now a fact of life that e-mail traffic is largely spam, unwanted solicitations for your time and money, if not worse. I recall in the days of the mailbox that spam was the latest sweepstakes offer. That’s quite tame compared to the dozens, if not hundreds, of daily spam offers we encounter. Spam cannot be avoided, but it can be controlled.
This does not have to be so. The most effective way to control spam is to note your internet behavior. Most people have one e-mail address, whether it corresponds to a friend, a bank or the guy needing money for his Nigerian grandmother. There is no better solution than to divide up your e-mail into unique e-mail addresses. (This is discussed at length in “A Method to the Madness.”)
This article focuses on how to effectively use spam filters. And it is a journey I have undertaken to understand spam filtering. Like just about everyone who reads this blog, I had one personal e-mail address. I was between jobs so I was hitting a lot of job sites on the web. It was then that I realized some were not quite what they appeared to be. When I began working at the University of Alaska (UAS) I had my personal e-mail address (which was used primarily for consulting work) forwarded to my work address. Before long the UAS account was being hammered by “job opportunities.” To add fuel to the fire, this was at a time when a faculty member’s e-mail address was posted onto a web page. Filtering, at this point, was a desperate battle of survival. Mix in about a 50-100 students, message management was a nightmare.
Introducing Filtering
Filtering has come a long ways since 2003 when I moved up to Alaska. I picked up on it quite readily. I started teaching the concept in security classes. I have seen various tools that provide filtering at different levels. For you, the average user, about all you see are the junk mail controls on your e-mail software. There is more to filtering than that. Filtering is done at several levels.
- Your Internet Provider or Host
- Your mail server
- Your e-mail client software
For most folks, what they see day-to-day is their e-mail client software and they’ll see a folder called “Junk” or “Spam”. What they don’t see is that Internet providers and hosting services (like 1and1.com) have been utilizing anti-spam measures of their own.
- Spammers need an e-mail server to do their work. The message must start from somewhere. That is getting harder to do these days using conventional channels. Mail service providers have been utilizing digital certificates to authenticate who they are, which makes it more difficult to service traffic from rogue servers. Mail servers on the Internet send messages to “relay servers”, which in turn are capable of detecting spam traffic and blocking abusers.
- Mail service squelching eliminates bulk e-mails. Most people do not encounter this problem until they volunteer to send newsletters to the 100 member gardening club. That’s when they discover an exciting new feature from the Internet provider – squelching. The messages start to drag, then get very inconsistent, and then get corrupted. You go to your provider’s web site and see in very fine print – “Send messages to as many as 50 recipients.” Once you go over that limit, the message delivery rate is sent to the bottom of the pile as messages may or may not be delivered. In other words, your Internet provider is not in the business of bulk mail.
From data I gathered during my days at UAS I detected that the UAS mail filter (which was my “Internet provider” so-to-speak) was filtering about 1500 messages a week for my account! They provided faculty and staff with a tool to check theses messages which provided a great deal of insight regarding the volume of spam. And that holds true for what your Internet provider these days encounters. Messages, which are unambiguously spam, are zapped before it ever gets to your mailbox.
The second layer of filtering is with your e-mail server. Most people have only an Internet provider, but if you have a hosted site ( like for your personal web page or business ), you will notice that your e-mail service has a filtering feature that affects all the people who are listed under your domain. If you had an address such as juneauflowers.com, and you had 12 employees, you can set spam filtering that affects all employees. This can remove another significant level of messages in which your employees may be tempted to open. You may also note that tools like SpamAssassin may be employed at the server-level.
No one is more aggressive at doing this than government web sites and high-security business sites. In my work with volunteer organizations, I implore people, over and over again, do not list your government office e-mail address. Invariably, newsletters are blocked by mail filters. If you subscribe to an e-mail server, you can also control quite specifically the type of traffic that comes to your employees.
The third layer is your e-mail client, the software you use on your computer or smartphone. You may have noticed that your mailbox may have a folder called “Junk” or “Spam”. These folders are used to collect spam and deposit into Junk folders. You usually get a message with a summary of the filtered messages. If you discover this is an error, you can right-click on the message and mark it “Not Junk”. Below is an example how you configure Thunderbird to filter junk mail, as well as decipher e-mail scams and messages with viral payloads.
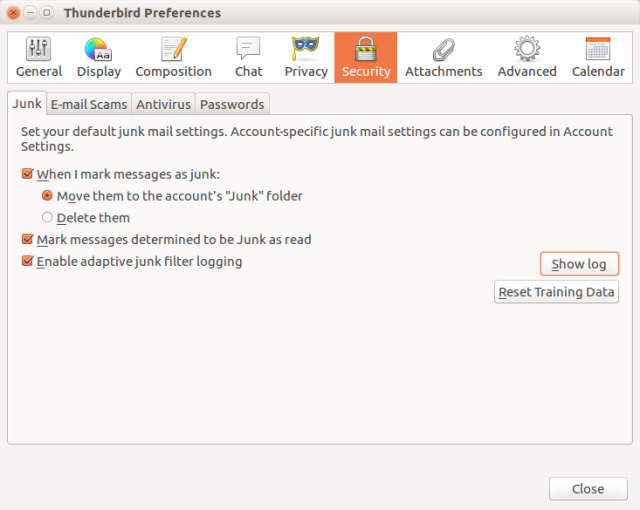
What is interesting about this layer is that you are introduced to the fact that an e-mail client is “trained” to identify junk mail. In reality, the spam filters of your e-mail server are also “trained,” albeit at a different level. Your spam filter is asking you to move into the Spam/Junk folder any message you do not trust or want. The next time that message arrives, it may see a similar message in the Spam/Junk folder and automatically mark the message as spam. Be patient. It may take a while for the software to learn. Another thing to note is read carefully which messages are being filtered in the event a sender you care about gets marked as “junk.” For example, my health care insurance provider had, for some odd reason, their messages filtered. The solution was to right-click over the message and mark it as “Not Junk”.
The fourth layer are “rules”. Thunderbird, my e-mail software, calls it “Message Filtering” while Outlook calls it “Rules”. In both cases, you have the ability to filter out messages based on who they come from or specific phrases. This is the last defense of filtering where all other measures fail. This feature is not only for spam, but for doubtful messages, or for general, routine messages that clutter up your mailbox and you wish to keep them out of the Inbox. As an enterprise administrator, my mailbox is pounded by automated messages. These are all handled by rules, which direct these messages to specific folders. This enables me to communicate more effectively with my colleagues while also tracking notifications.The final filter is yourself. Be smart. If the message is unsolicited, use common sense. What do you know about a grandmother in Nigeria? Are there links in the message which are different than the sender. Is their an attachment from somebody you do not know. When in doubt, delete it.

In Conclusion
As I said at the beginning, learning the art of spam filtering is a journey. Take some time, beginning with your e-mail software. See which features it provides for filtering and virus protection. See which features your Internet provider employs for spam filtering. Make one change at a time and measure how it affects your e-mail traffic.
© Copyright 2016 to Eric Niewoehner
